Wifite : Hacking Wifi The Easy Way : Kali Linux
Wifite
While the aircrack-ng suite is a well known name in the wireless hacking , the same can't be said about Wifite. Living in the shade of the greatness of established aircrack-ng suite, Wifite has finally made a mark in a field where aircrack-ng failed. It made wifi hacking everyone's piece of cake. While all its features are not independent (eg. it hacks WPS using reaver), it does what it promises, and puts hacking on autopilot. I'm listing some features, before I tell you how to use wifite (which I don't think is necessary at all, as anyone who can understand simple English instructions given by Wifite can use it on his own).
Features Of Wifite
- Sorts targets by signal strength (in dB); cracks closest access points first
- Automatically de-authenticates clients of hidden networks to reveal SSIDs
- Numerous filters to specify exactly what to attack (wep/wpa/both, above certain signal strengths, channels, etc)
- Customizable settings (timeouts, packets/sec, etc)
- "Anonymous" feature; changes MAC to a random address before attacking, then changes back when attacks are complete
- All captured WPA handshakes are backed up to wifite.py's current directory
- Smart WPA de-authentication; cycles between all clients and broadcast deauths
- Stop any attack with Ctrl+C, with options to continue, move onto next target, skip to cracking, or exit
- Displays session summary at exit; shows any cracked keys
- All passwords saved to cracked.txt
- Built-in updater: ./wifite.py -upgrade
I find it worth mentioning here, that not only does it hack wifi the easy way, it also hack in the best possible way. For example, when you are hacking a WEP wifi using Wifite, it uses fakeauth and uses the ARP method to speed up data packets (I wrote a full length post about something which it does automatically!).
Hacking WEP network
If you've followed my previous posts on Hacking Wifi (WEP), you know there's a lot of homework you have to do before you even start hacking. But not here. With Wifite, its as easy and simple as a single command.
wifite -wepYou might even have used the command
wifiteIf you see any error at this stage move to the bottom of the page for troubleshooting tips. If your issue is not listed please comment. We reply within a day.
The -wep makes it clear to wifite that you want to hack WEP wifis only. It'll scan the networks for you, and when you think it has scanned enough, you can tell it to stop by typing ctrl+c. It'll then ask you which wifi to hack. In my case, I didn't specify -wep so it shows all the wifis in range.
You can also select all and then go take a nap (or maybe go to sleep). When you wake up, you might be hacking all the wifi passwords in front of you. I typed one and it had gathered 7000 IVs (data packets) within 5 mins. Basically you can except it to hack the wifi in 10 mins approx. Notice how it automatically did the fake auth and ARP replay.
Here are a few more screenshots of the working of Wifite, from their official website (./wifite.py is not something that should bother you. You can stick with the simple wifite. Also, specifying the channel is optional so even the -c 6 was unnecessary. Notice that instead of ARP replay, the fragmentation attack was used, using -frag) -
Hacking WPS wasn't fast (it took hours), but it was easy and didn't require you to do anything but wait.Note, the limitation that many reader on my blog are beginners forbid me from introducing too many attacks. I made a tutorial about ARP replay attack, and that too was detailed as hell. However, Wifite makes it possible for you to use any method that you want to use, by just naming it. As you saw in the screenshot above, the fragmentation attack was carried out just by typing -frag. Similarly, many other attacks can be played with. A good idea would be to execute the following-
wifite -helpThis will tell you about the common usage commands, which will be very useful. Here is the list of WEP commands for different attacks-
WEP
-wep only target WEP networks [off]
-pps <num> set the number of packets per second to inject [600]
-wept <sec> sec to wait for each attack, 0 implies endless [600]
-chopchop use chopchop attack [on]
-arpreplay use arpreplay attack [on]
-fragment use fragmentation attack [on]
-caffelatte use caffe-latte attack [on]
-p0841 use -p0841 attack [on]
-hirte use hirte (cfrag) attack [on]
-nofakeauth stop attack if fake authentication fails [off]
-wepca <n> start cracking when number of ivs surpass n [10000]
-wepsave save a copy of .cap files to this directory [off]
As you can see, its the same thing as is there on the help screenshot. Play around with the attacks and see what you can do. Hacking WPA without WPS wouldn't be that easy, and while I don't usually do this, I'm providing a link to an external website for the tutorial . This is the best WPA cracking tutorial I've seen, and I can't write a better one. It's highly detailed, and I'm just hoping I don't lose my audience to that website. Here is the tutorial - Cracking Wifi WPA/WPA2 passwords using pyrit cowpatty in Kali Linux
Troubleshooting
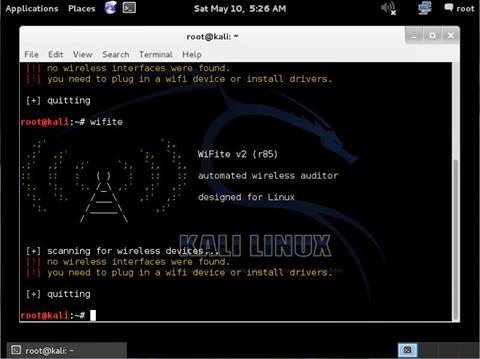
Wifite quits unexpectedly, sating "Scanning for wireless devices. No wireless interfaces were found. You need to plug in a wifi device or install drivers. Quitting."
You are using Kali inside a virtual machine most probably. Virtual machine does not support internal wireless card. Either buy an external wireless card, or do a live boot / side boot with Windows. Anything other than Virtual machine in general.
WPA/WPA-2 Wifi Hacking click here
WEP Wifi Hacking click here :
WPA/WPA-2 Wifi Hacking click here
WEP Wifi Hacking click here :






3 comments
commentsHello Shivam,
ReplyI believe I have network issues:
I am using Kali 2.0 on a raspberry Pi3 to run Wifite R87
My outside USB wifi card is an Alfa AWUS051NH, and its current port is wlan1
network sounds good as iwconfig is returning me:
~# iwconfig
tun0 no wireless extensions.
wlan0 IEEE 802.11bgn ESSID:off/any
Mode:Managed Access Point: Not-Associated
Retry short limit:7 RTS thr:off Fragment thr:off
Encryption key:off
Power Management:on
lo no wireless extensions.
wlan1mon IEEE 802.11abgn Mode:Monitor Frequency:2.462 GHz Tx-Power=20 dBm
Retry short limit:7 RTS thr:off Fragment thr:off
Power Management:off
eth0 no wireless extensions.
I can perfectly run wifite interface:
when I start
wifite -wep -i wlan1
I get this
[+] scanning (wlan1mon), updates at 5 sec intervals, CTRL+C when ready.
NUM ESSID CH ENCR POWER WPS? CLIENT
--- -------------------- -- ---- ----- ---- ------
1 NUMERICABLE-19BA 11 WEP 32db n/a clients
2 (14:0C:76:FE:E2:70) 11 WEP 30db n/a
[0:02:18] scanning wireless networks. 2 targets and 648 clients found
NUM ESSID CH ENCR POWER WPS? CLIENT
--- -------------------- -- ---- ----- ---- ------
1 CABLEBOX-19BA 11 WEP 32db n/a clients
2 (14:0C:76:FE:E2:70) 11 WEP 30db n/a
[+] select target numbers (1-2) separated by commas, or 'all': 1
[+] 1 target selected.
[0:10:00] preparing attack "CABLEBOX-19BA" (C0:3F:0E:D8:7C:23)
[0:10:00] attempting fake authentication (5/5)... failed
[0:10:00] attacking "CABLEBOX-19BA" via arp-replay attack
[0:10:00] attempting fake authentication (5/5)... failed
[0:10:00] attacking "CABLEBOX-19BA" via chop-chop attack
[0:09:54] attack failed: unable to generate keystream
[0:10:00] attempting fake authentication (5/5)... failed
[0:10:00] attacking "CABLEBOX-19BA" via fragmentation attack
[0:09:54] attack failed: unable to generate keystream
[0:10:00] attempting fake authentication (5/5)... failed
[0:10:00] attacking "CABLEBOX-19BA" via caffe-latte attack
[0:09:54] attack failed: aireplay-ng exited unexpectedly
[0:10:00] attempting fake authentication (5/5)... failed
[0:10:00] attacking "CABLEBOX-19BA" via p0841 attack
[0:09:30] attack failed: aireplay-ng exited unexpectedly
[0:10:00] attempting fake authentication (5/5)... failed
[0:10:00] attacking "CABLEBOX-19BA" via hirte attack
[0:07:33] captured 0 ivs @ 0 iv/sec
[0:00:00] attack complete: failure
[+] 1 attack completed:
[+] 0/1 WEP attacks succeeded
[+] quitting
wifite is acting like it cannot perform any injection
the results are always the same
Where is my mistake or the error??
Kind regards
1 - forget the name changing between numericable and cablebox, this is not where the error comes from, it was just renamed to perform more tests, I just mixed some lines doing copy/paste to answer you
Reply2 - this blogspot is changing :0 into emoticons, it should be read and attached ": 0 " instead of :0
:)
Reply